Table of contents
Open Table of contents
Intro
I wrote earlier in 2020 how I can cross-post articles to Twitter and LinkedIn with iOS Shortcuts and Azure Logic Apps. Now seems to be a good time to revisit that.
I have been trying to be more active on LinkedIn nowadays (again), and getting my feet wet on Mastodon. Then again I have pretty much stopped using Twitter altogether, but why not share my content on that platform too. All and all, I spend way less time on social media than I used to, and this has been a very good decision for me.
In the previous article from 2020 I included the iOS Shortcut creation in the same article, this time I will focus solely on the Azure Logic App part of the solution. Maybe I will revisit the Shortcut part later.
Prerequisites
- Azure subscription
- Accounts on LinkedIn, Mastodon and Twitter
Azure Logic Apps
Azure Logic Apps is Microsoft’s answer to low-code integration development / orchestration. Microsoft itself describes Logic Apps as so:
Azure Logic Apps is a leading integration platform as a service (iPaaS) built on a containerized runtime. Deploy and run Logic Apps anywhere to increase scale and portability while automating business-critical workflows anywhere.
Quite grand, but that’s what they say :) I still will not fall in to the trap of discussing whether or not low-code is the future of integration development or the right choice, or a complete lie. As far as my own experience goes, low-code is not a silver bullet to cater all possible needs. Then again, it definitely has its use cases, this example here being one of them. No point to start coding an app “with actual code”, when all the necessary actions are available out of the box, at a really tiny cost.
Note on the costs: Azure Logic Apps are billed by the Action execution and Connector call in the Consumption Plan, so this is something to keep in mind when designing and developing these low-code integrations. At the time of writing, one Action execution in West Europe region costs 0.000024 €, and Standard Connector 0.000118 € per call. Especially if you use loops to process large datasets, pay special attention to this as they might get expensive!
Obtaining and storing Mastodon access token
Unlike LinkedIn and Twitter, at the time of writing Azure Logic Apps don’t have a Mastodon connector. Because of this, we will need to use a standard HTTP action to make POST request to our Mastodon instance’s API endpoint. And in order to do this, we need to create new Mastodon application under our account, and obtain an access token. Then, we will store that token securely in Azure Key Vault. Let’s get to work.
-
Create new Mastodon app and obtain the access token Sign in to your Mastodon instance on web, and navigate to
Preferences > Development > New application. On the settings of the app:- give the application a name (Note: this name will be visible on the posted status messages)
- add application website for your app (Note: this also needs to be a functioning URL)
- for scopes select only
write:statuses, since that’s the only action we need
Hit Submit, and then open your brand new app. Copy the access token.
-
Create Azure Key Vault We will be storing the access token securely in Azure Key vault, so we need to create that first:
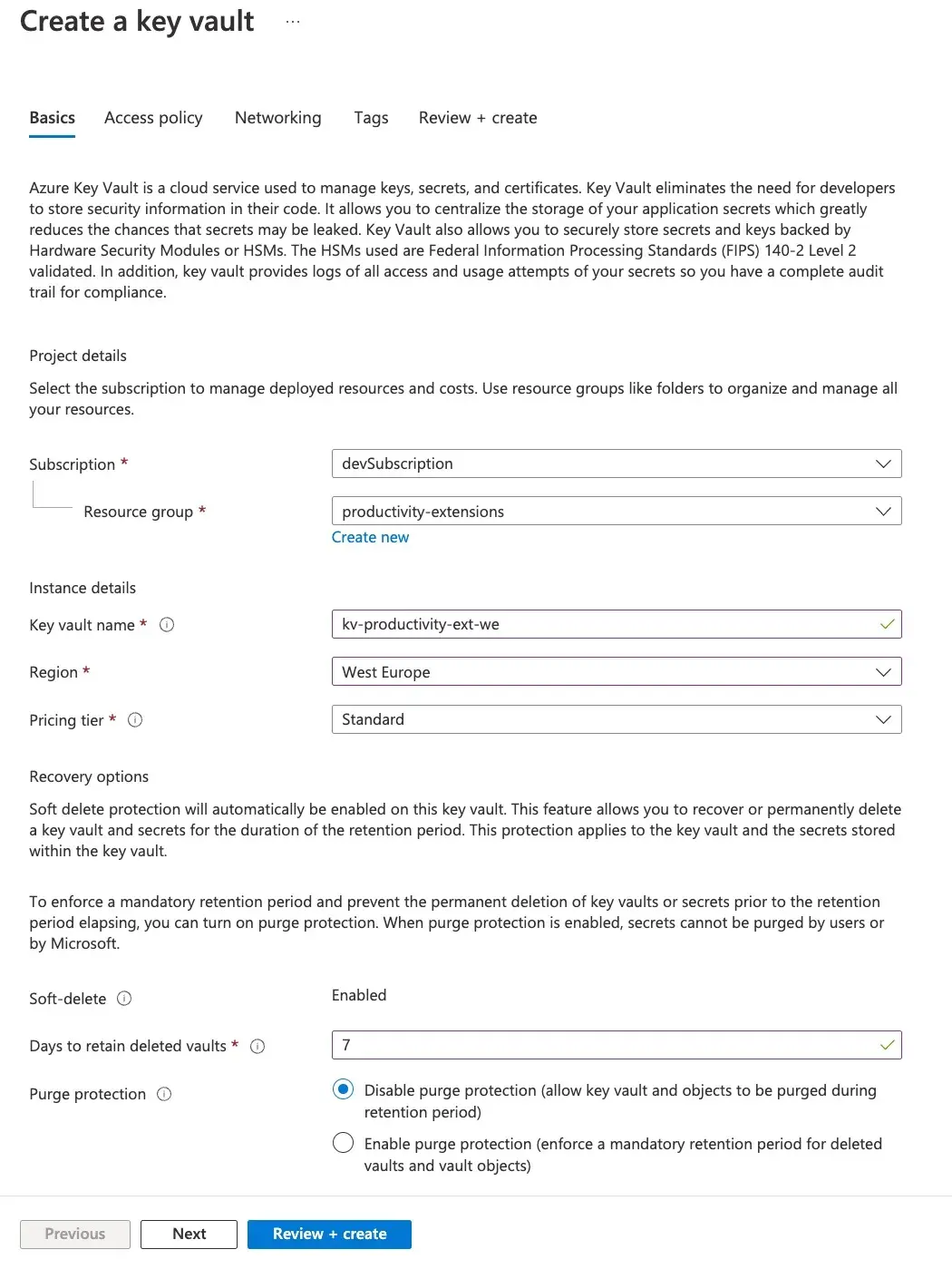 Please make sure that you create the Key vault and Logic App in the same Subscription and Azure region. After filling in the details, hit
Please make sure that you create the Key vault and Logic App in the same Subscription and Azure region. After filling in the details, hit Next.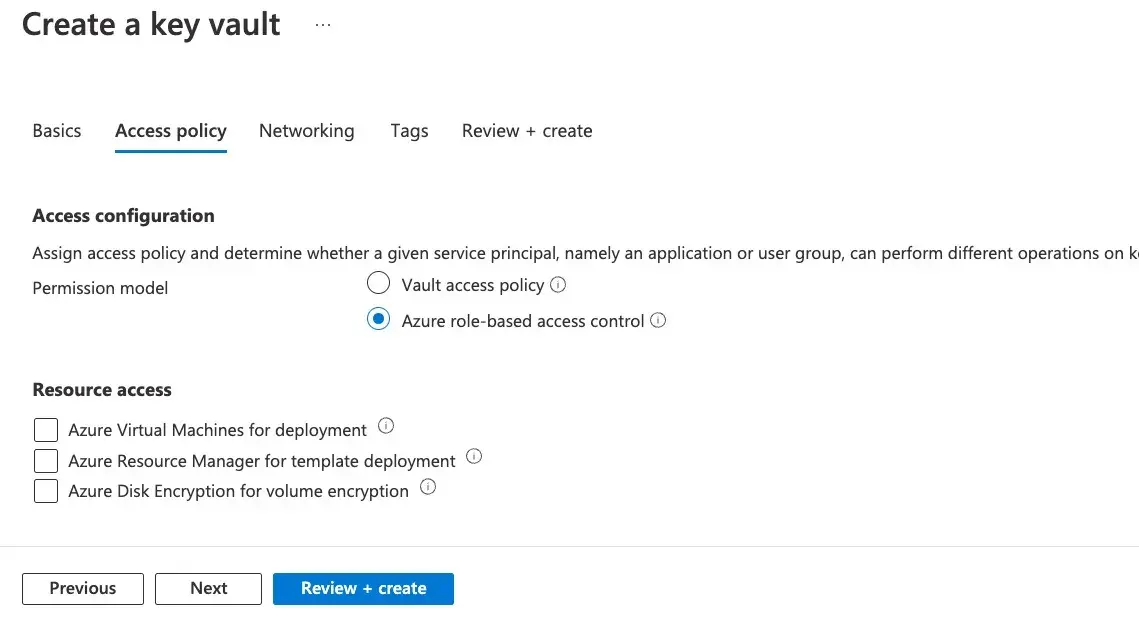 We want to use Azure RBAC as permission model. After selecting that, hit
We want to use Azure RBAC as permission model. After selecting that, hit Review + Createand wait for the resource to be created. -
Store new secret In order to store a new secret, we first need to give yourselves a permission to do so. You see, even though we might have Owner role to Azure resources, that does not give us data plane access to secrets themselves. So, lets go and give ourselves a RBAC role
Key Vault Administrator.After that we can create a new secret:
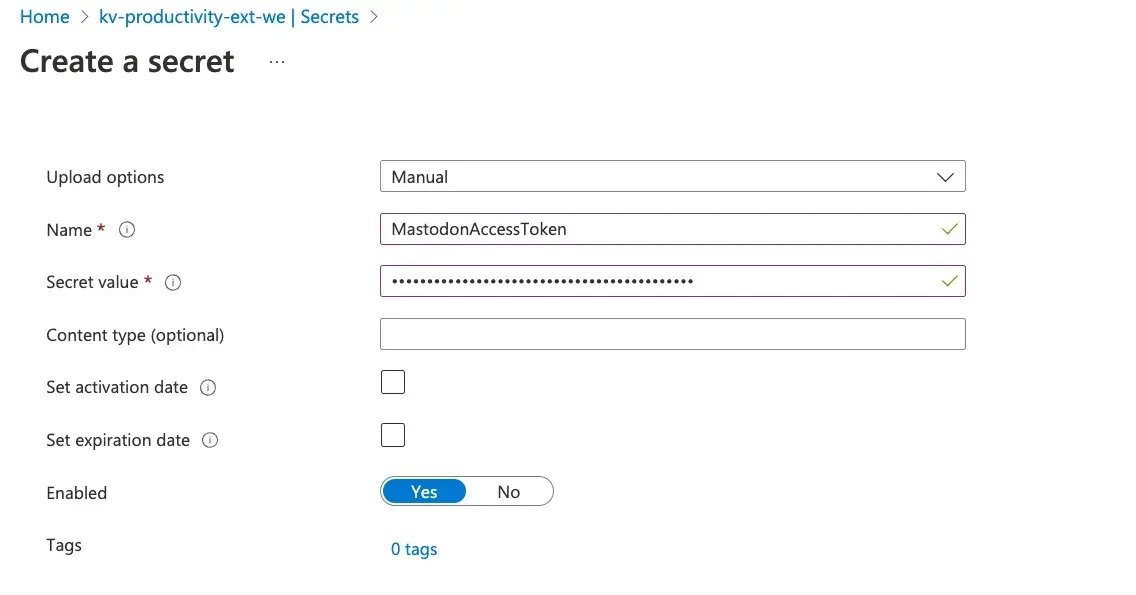
-
Authorize the Logic App to read the secret We will be using a System assigned managed identity to authorize the Logic App to read the secret. First, enable System assigned managed identity for the Logic App under
Settings > Identity: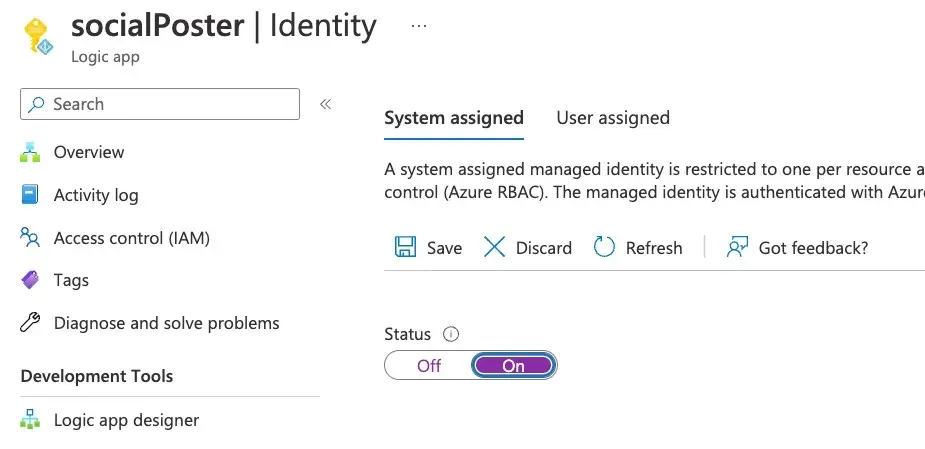 If you did not create the Logic App already before this step, go on an create a new Logic App which is triggered by a HTTP request and which is using Consumption plan and then follow along again.
Then, back at the Key vault IAM, add the role
If you did not create the Logic App already before this step, go on an create a new Logic App which is triggered by a HTTP request and which is using Consumption plan and then follow along again.
Then, back at the Key vault IAM, add the role Key Vault Secrets Userfor the created Managed identity.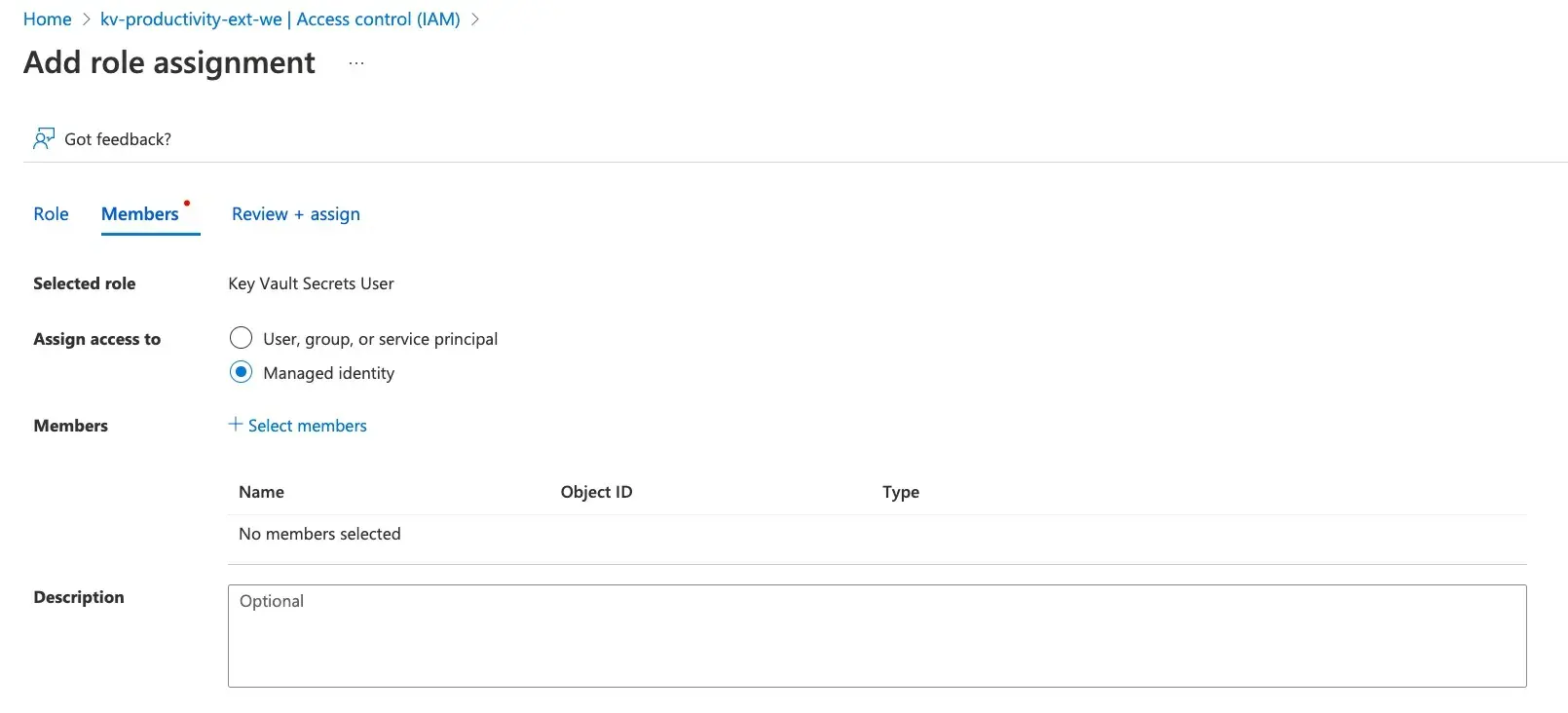 Now we are ready to go back to the Logic App and start implementing the flow!
Now we are ready to go back to the Logic App and start implementing the flow!
Azure Logic App: Social Poster v2
Azure Logic Apps are handy in the way that we get a logic diagram out of the box, since that is the implementation of the whole app (although there is a json view available too). In all its complexity, our Social Poster v2 app looks like this:
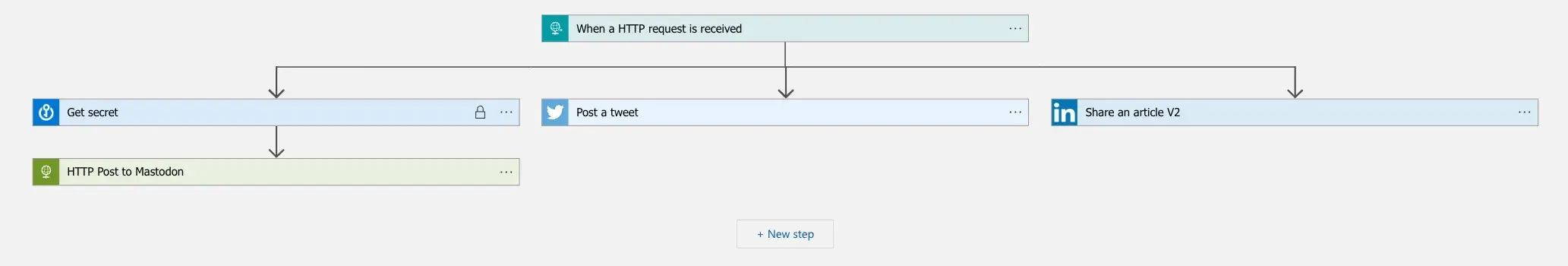
The actions will be run in parallel. In this case it seems logically sensible option since the actions do not depend on the previous action’s results.
Let’s break the flow down:
-
When a HTTP request is received
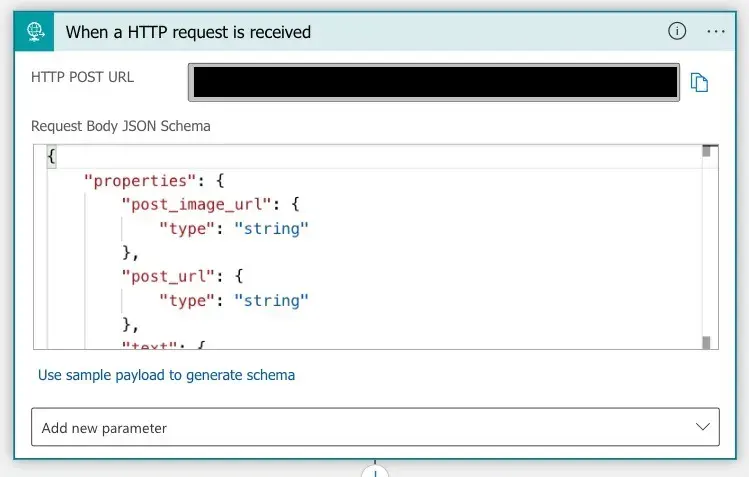 This flow is triggered by an HTTP POST request, with a specific JSON payload, such as:
This flow is triggered by an HTTP POST request, with a specific JSON payload, such as:{ "title": "New article: Signing git commits with SSH key", "text": "GitHub started supporting SSH commit verification on August 2022 #GitHub #Git #development #DevOps", "post_url": "https://janik6n.net/signing-git-commits-with-ssh-key", "post_image_url": "https://janik6n.net/images/post_covers/seal-signature.jpg" }The POST request body JSON Schema must be defined in order for us to be able to use the data as variables later on. The JSON Schema corresponding to our payload is as follows:
{ "properties": { "post_image_url": { "type": "string" }, "post_url": { "type": "string" }, "text": { "type": "string" }, "title": { "type": "string" } }, "type": "object" } -
Post a status to Mastodon:
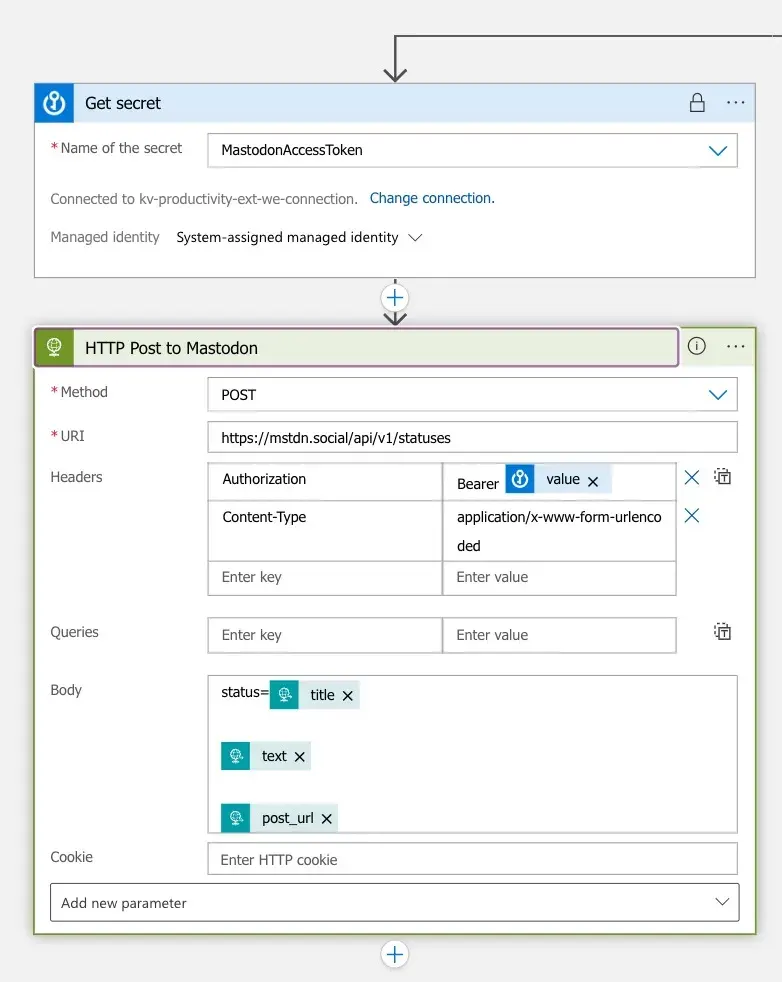 First, we need to get the access token from the Key vault created earlier. In order to avoid leaking the secret value to Logic App logs during execution, make sure to turn on the
First, we need to get the access token from the Key vault created earlier. In order to avoid leaking the secret value to Logic App logs during execution, make sure to turn on the Secure Outputssetting of the action: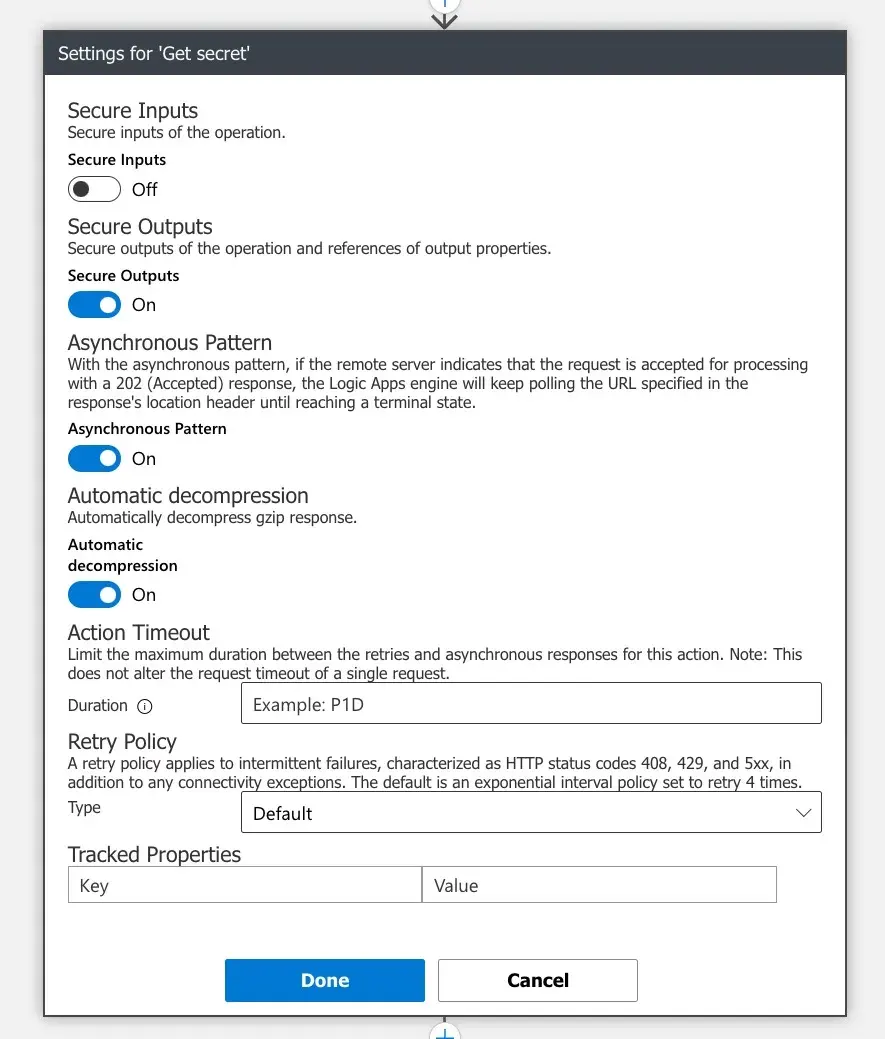 To post a status message to Mastodon, we will be using a standard HTTP action to call the API endpoint of our Mastodon instance,
To post a status message to Mastodon, we will be using a standard HTTP action to call the API endpoint of our Mastodon instance, https://mstdn.social/api/v1/statusesin this case. -
Post a tweet:
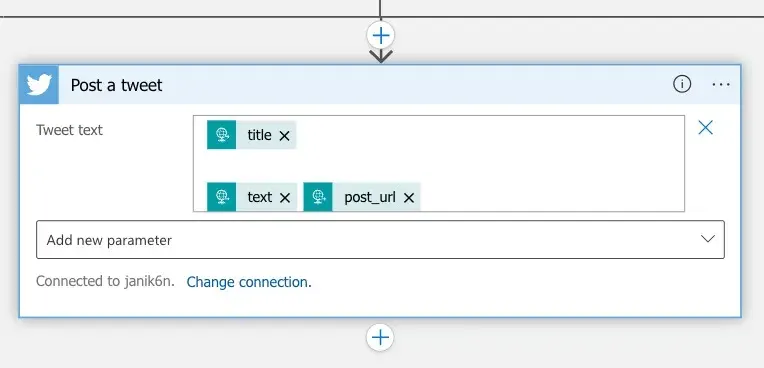 When you add the Twitter connector, you must authenticate with the standard Twitter OAuth2 flow using your Twitter credentials. Azure will store the tokens securely as API Connection resource. API Connections are shared within the Subscription and Region, so the same API connection can be used in multiple Logic Apps.
When you add the Twitter connector, you must authenticate with the standard Twitter OAuth2 flow using your Twitter credentials. Azure will store the tokens securely as API Connection resource. API Connections are shared within the Subscription and Region, so the same API connection can be used in multiple Logic Apps.Please keep in mind the maximum length of the tweet, which is 280 characters at the time of writing! The calculation of the character length is not as straightforward as it may seem. This Logic App assumes, that the client calling this flow will take care of the user input validation. In addition, the Logic Apps Twitter connector has some quite strict limitations on top of this, for example you cannot
@mention anyone, and these characters will be removed altogether. Please have a look at the links at the end of this article for detailes. -
Share an article on LinkedIn:
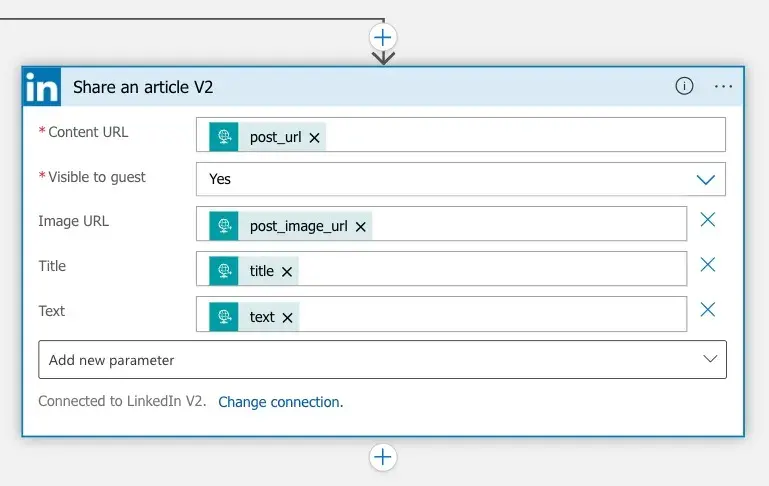 When you add the LinkedIn V2 connector, you must authenticate with the standard LinkedIn OAuth2 flow using your LinkedIn credentials. Same as above, the tokens will be stored as API Connection for further use. Note: The tokens will expire eventually, and the action will fail with an error. In this case, you will need to re-authenticate to refresh the tokens.
When you add the LinkedIn V2 connector, you must authenticate with the standard LinkedIn OAuth2 flow using your LinkedIn credentials. Same as above, the tokens will be stored as API Connection for further use. Note: The tokens will expire eventually, and the action will fail with an error. In this case, you will need to re-authenticate to refresh the tokens.
Logic Apps authentication & authorization
The Logic Apps’ public URL is generated, when you save the Logic App for the first time. Azure Logic Apps uses the concept of Shared Access Keys, which are presented as SAS URLs. This is what you get, when the Logic App is saved for the first time. In other words: Anyone having the complete SAS URL will be able to successfully call your Logic Apps flow. Please do not share the URL with anyone, who should not have it! If you need to regenerate the SAS URL (key part), you can easily do so in the Logic Apps’ Settings, under Access keys.
Testing the Logic App
We could use any HTTP client out there to issue a test request to our new Logic Apps’ HTTP endpoint. Simply:
- Send a HTTP POST request to the Logic Apps’ URL.
- Remember to set header
Content-Typetoapplication/json. - Enter body as described earlier in this article.
After successful submission, the execution logs can be seen in Azure portal in the Logic App’s Run history (more details can be seen by expanding each action):
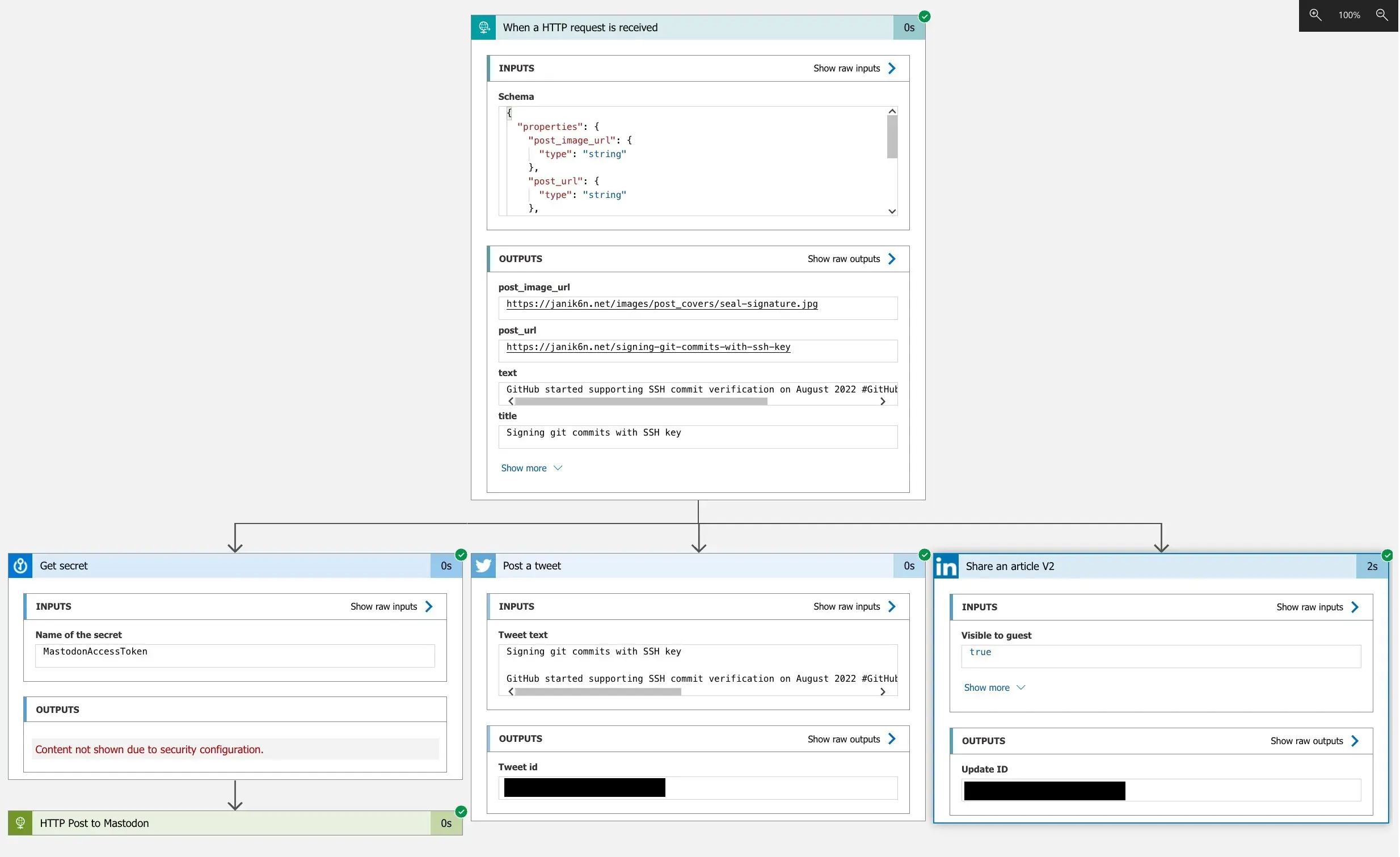
And the end results on Mastodon:
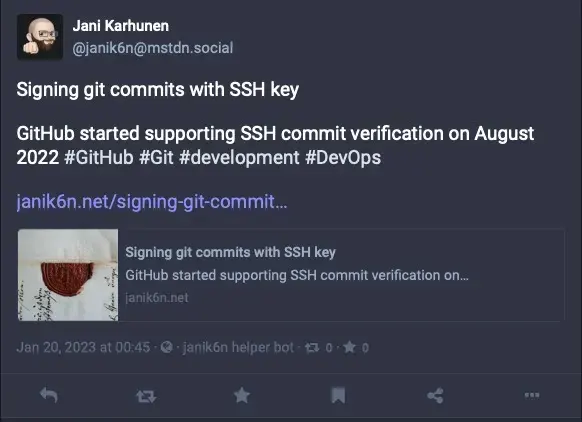
… and on LinkedIn:
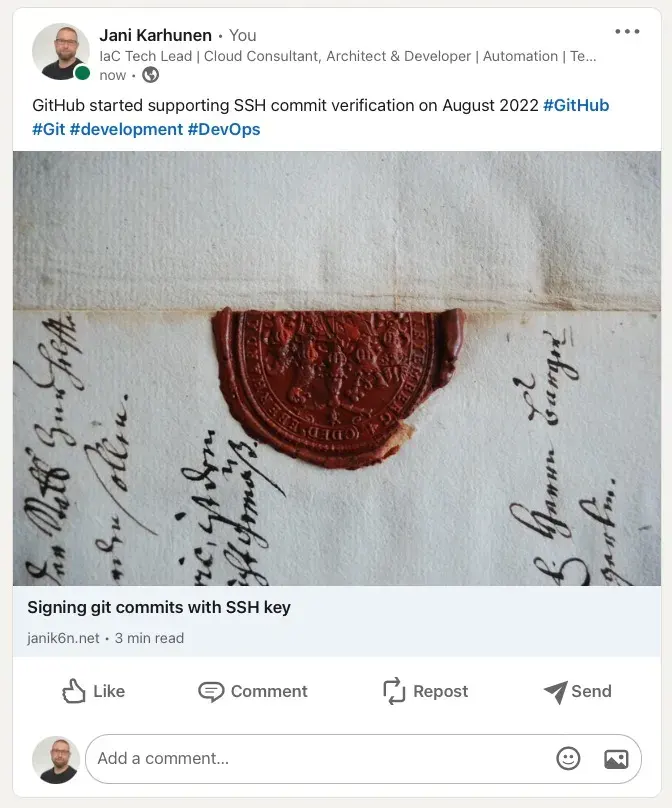
… and finally on Twitter:
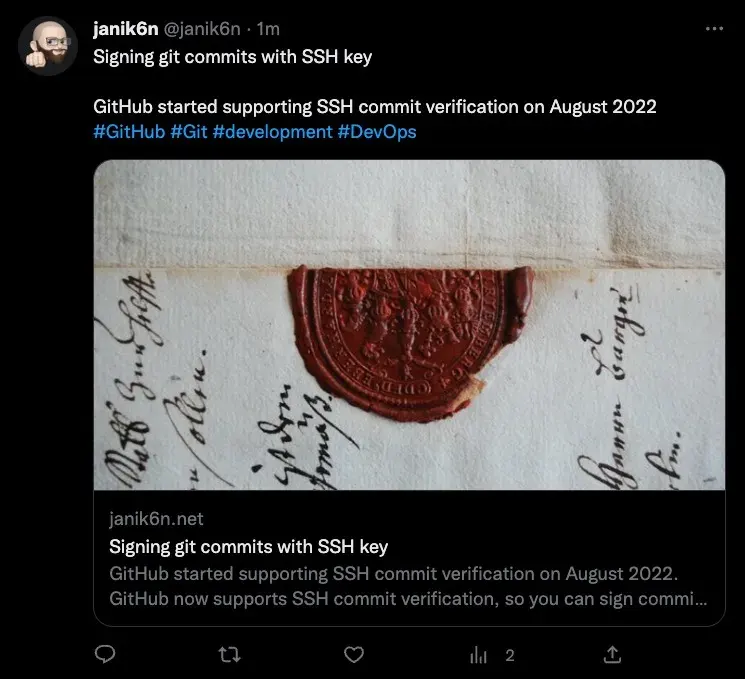
Now we just need to write something cool to be shared!
Recap
In this article I showed hands-on how we can utilize Azure’s low-code tools to automate cross-posting to various social media platforms. Hopefully this article gave you some ideas how to use such tools for your own use cases by presenting one real-life example.